Introduction to containers
About Me
- I am Mohammed Daoudi AKA iduoad
- I am a devops engineer @Nimbleways
- I am programming enthusiasts (Go/Python)
- I taught a semester of Database Security @Sorbone university Paris
- I love cinema
What are containers ?
A little bit about container history
1979-90s: The inception
- It is all about process isolation.
- 1979: Unix V7 introduced
chroot.chrootsegregates file access for unix processes.
- 1982: BDS introduced
chroot. - 2000: FreeBSD introduced
jails.
90s-00s: The downfall of container
- Windows is here !!
- Windows is not compatible with UNIX.
- We need to run Windows on Unixes, and the other way too.
- The rise of hardware virtualization.
- Hardware virtualization is about machines (CPU, RAM, Devices, …)
- Virtual machines have nothing to do with containers.
early 00s: Renaissance - The age of VPS
- The web is hot = High demand for web hosting !!
- Better resource management + process isolation vs Security + true isolation.
- 2001: Linux VServer
- 2004: Solaris Containers
- 2005: Open VZ (Open Virtuzzo)
2008: Finally Linux container - LXC
- 2006: Google contributed
Cgroupsinto the linux kernel. - 2008: LXC is here: the first complete implementation of a linux container manager.
- LXC is a system container manager.
- Introduced container images.
- LXC is Linux native.
2013: DOCKER !!
- 2011-2013: Warden, LMCTFY, …
- 2013: Docker is here
- Docker started as a PAAS company (like heroku).
- Docker used LXC as a backend, then moved to libcontainers after.
- Docker solves a new problem.
2015-: The golden age of cloud native
- 2015: Open Container Initiative
- 2015: Kubernetes
- 2015: Cloud Native Compute Foundation
- 2015-: Tons of container engines, runtimes and tools: podman, buildah, skopeo, crun, gVisor, katacontainers…
Linux containers under the hood
Linux processes
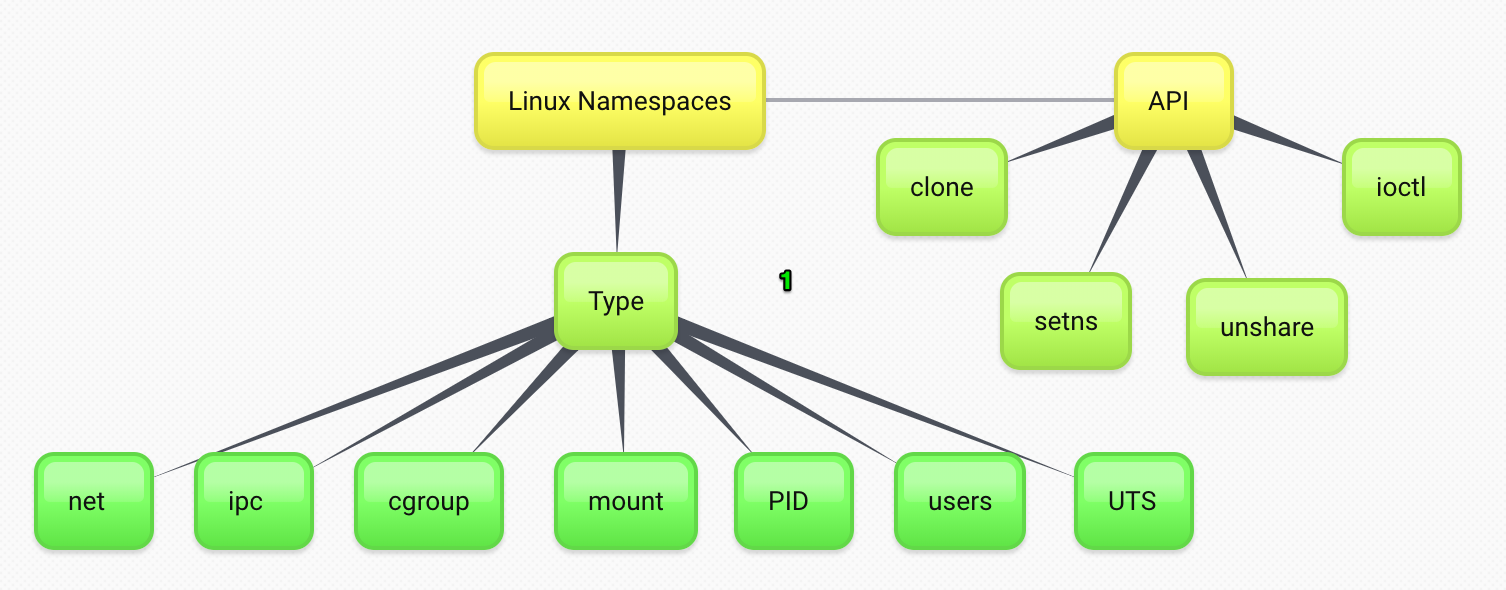
Linux Namespaces.
Namespaces are a feature of the Linux kernel that partitions kernel resources such that one set of processes sees one set of resources while another set of processes sees a different set of resources.
int clone(int (*fn)(void *), void *stack, int flags, void *arg, ...
/* pid_t *parent_tid, void *tls, pid_t *child_tid */ );
int unshare(int flags);
int setns(int fd, int nstype);
Linux Namespaces
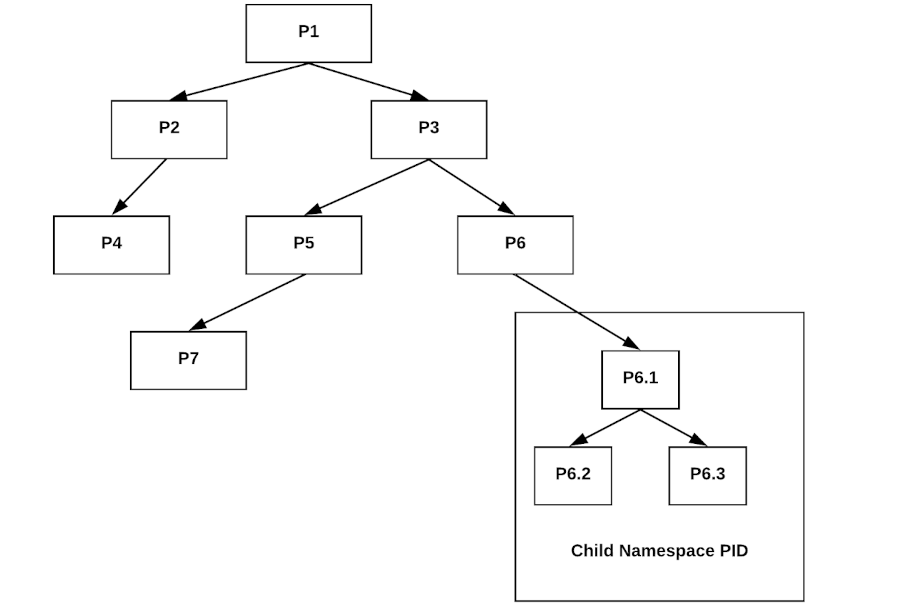
Linux Namespaces.
- PID namespaces
- UTS namespaces
- Mount namespaces
- Network namespaces
- User namespaces
- IPC, Date
Linux Namespaces.
Cgroups
cgroups is a Linux kernel feature that limits, accounts for, and isolates the resource usage of a collection of processes.
Security
- Linux Capabalities
- Seccomp
- SeLinux/AppArmor
Running containers
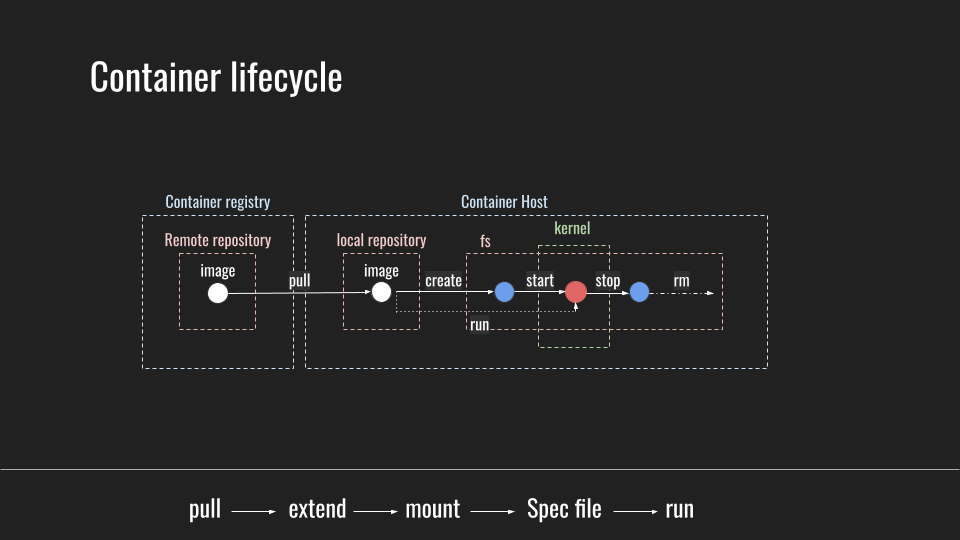
Container lifecycle
Case Studies
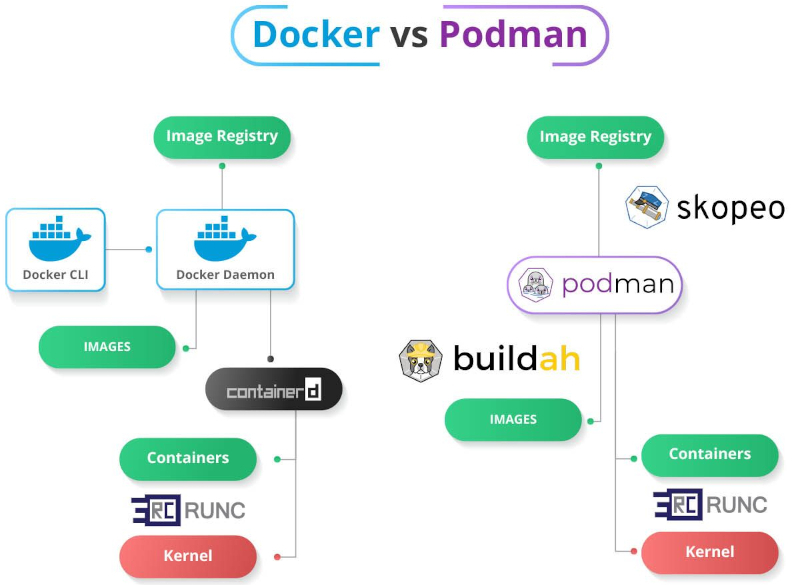
Docker
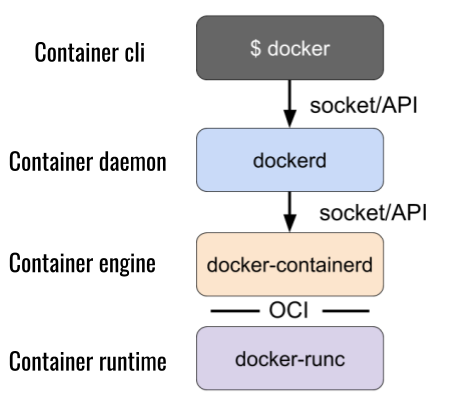
PBS (container-tools)
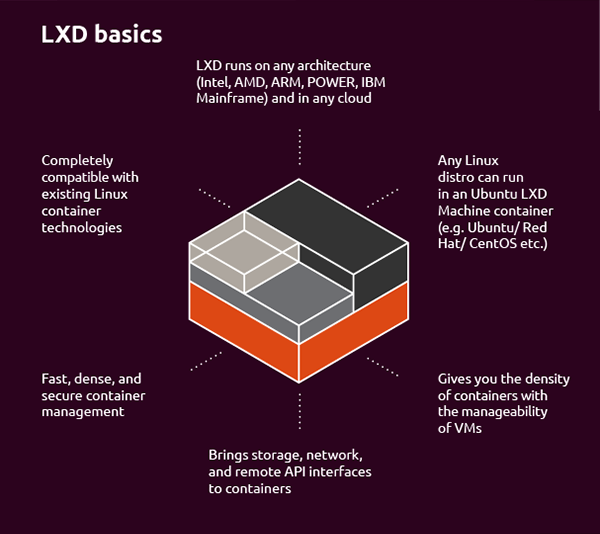
System container runtimes: LXC/LXD, OpenVZ …
Thank you
Let’s be friends! 🤗
Introduction to containers